The Unseen Threat: Understanding Modern Security Breaches
It’s a digital reality no business can afford to ignore: security breaches are not an abstract possibility, but a looming inevitability. The sophistication of today’s cybercriminals and the constantly evolving landscape of web technologies mean that even the most robust sites are potential targets. From e-commerce platforms to SaaS portals, breaches can originate from zero-day vulnerabilities, misconfigured cloud storage, compromised credentials, or even sophisticated phishing campaigns. The crucial first step to protection isn’t building an impenetrable fortress—because, frankly, such a thing does not exist—but rather, developing a mindset of vigilance and preparedness.
The real-world impacts of security breaches range from data theft and site defacement to massive financial losses and reputation damage. In recent years, we have seen global retail brands, hospitals, and even government agencies fall victim to attacks. Yet, the difference between organizations that survive and those that are devastated is rooted not in the breach itself, but in how swiftly and effectively they detect, respond, and recover.
Early Detection: How Breaches are Discovered in Practice
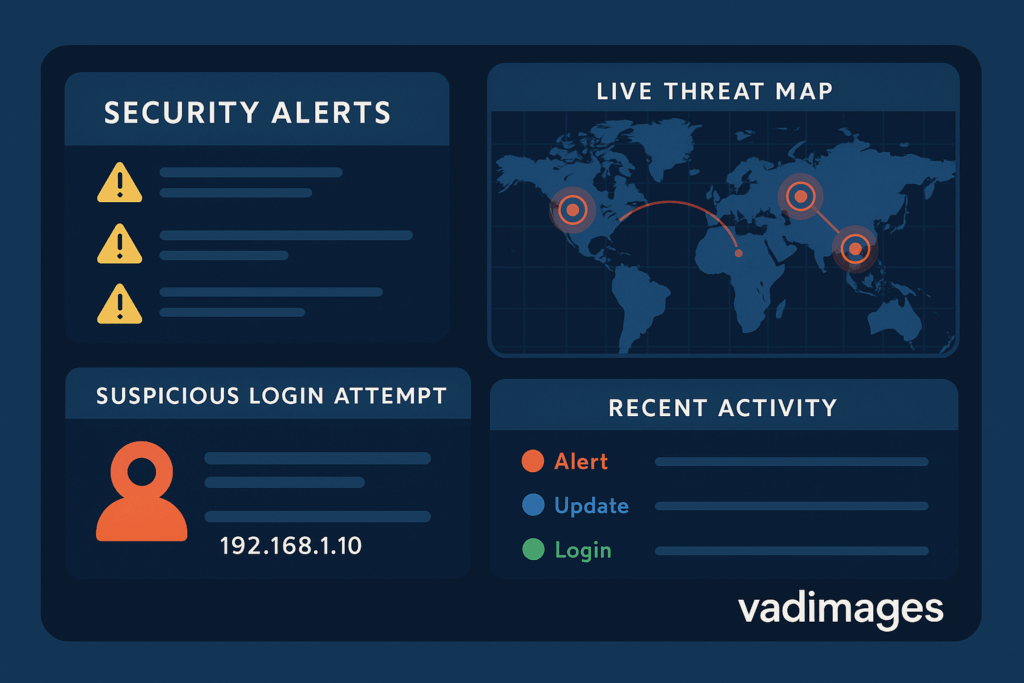
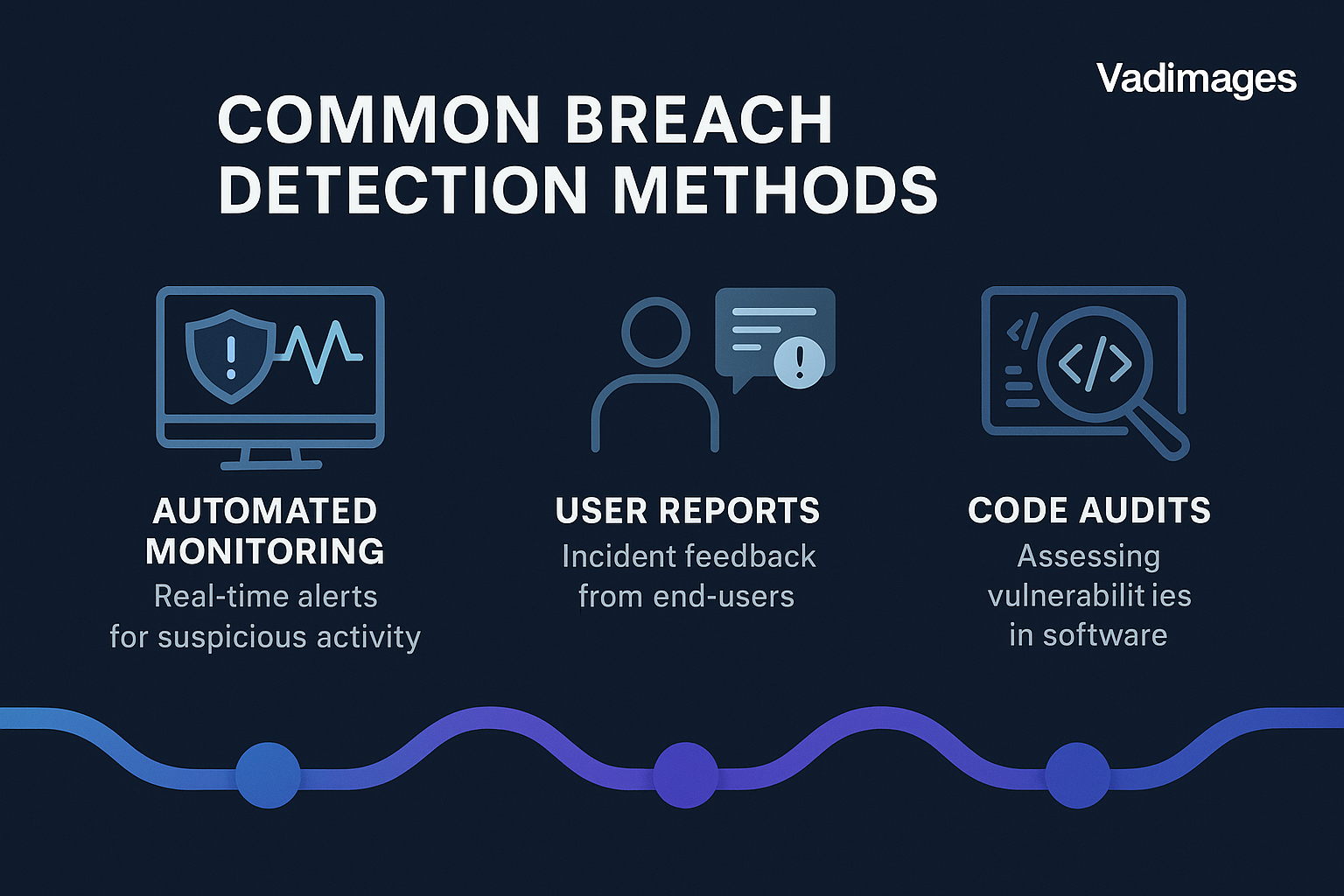
The detection of a breach rarely occurs at the moment the attacker gains access. More often, the initial compromise is subtle—sometimes lingering undetected for days, weeks, or even months. Effective breach detection relies on multiple layers of monitoring and analytics. Indicators of compromise (IoCs) may appear as unusual network traffic, unexpected administrative actions, unexplained changes to files, or even simple performance anomalies. Yet, in real-world scenarios, it is often a combination of automated systems and human vigilance that triggers the first alarm.
For example, consider a SaaS provider who suddenly detects a spike in API errors and failed login attempts late at night. Their security monitoring platform highlights the anomaly, flagging it for review. Upon investigation, the technical team uncovers evidence of credential stuffing—an attacker using stolen usernames and passwords from unrelated breaches to try to access accounts on their platform. Thanks to real-time monitoring and alerting, the breach is caught before any customer data is exfiltrated.
Other scenarios can be more insidious. In one well-documented case, an e-commerce company discovered a breach only after several customers reported fraudulent purchases using their saved payment data. The investigation revealed a vulnerability in a third-party plugin that allowed attackers to inject malicious code into the checkout page. The breach had persisted undetected for weeks, highlighting the importance of not just automated alerts, but also continuous code audits and user feedback loops.
Responding Under Pressure: Strategies for Minimizing Damage
Once a breach is detected, the clock starts ticking. The first priority is containment—stopping the attacker from causing further damage. This may involve taking affected systems offline, revoking access credentials, or disabling compromised APIs. But swift containment is only the beginning.
A structured incident response plan is vital. The best teams operate like an emergency crew: they know their roles, have rehearsed for crises, and work from a well-documented playbook. Real-world strategies include immediate isolation of compromised components, forensic data collection, and communication with key stakeholders—clients, users, regulatory bodies, and legal counsel as needed.
Vadimages brings experience from numerous client incidents, helping organizations avoid the chaos that often follows a breach. In one recent case, a logistics platform powered by Vadimages faced a ransomware attack that encrypted critical order data. Because Vadimages had implemented automated daily backups and a tested disaster recovery workflow, the site was restored within hours, with no ransom paid and minimal business disruption.
Effective response is about transparency as much as technology. Customers must be informed, regulatory requirements satisfied, and root causes addressed. This means not just technical recovery, but also proactive communication—turning a crisis into an opportunity to demonstrate professionalism and responsibility.

Building Resilience: The Long-Term Path to Security Confidence
Detecting and responding to breaches is not a one-time event, but an ongoing commitment. The organizations that thrive in the modern threat landscape are those who view security as a process—not a product. Regular penetration testing, employee security training, and post-incident reviews all contribute to continuous improvement.
Vadimages believes every website deserves world-class security, not just in the initial build but throughout its lifecycle. For e-commerce platforms, this may include secure payment gateway integrations, PCI DSS compliance audits, and robust customer notification systems. For SaaS providers, it means role-based access controls, encrypted data storage, and round-the-clock monitoring.
After an incident, a thorough post-mortem analysis should drive actionable improvements—patching exploited vulnerabilities, revising monitoring thresholds, and, when needed, updating legal and regulatory compliance strategies. At Vadimages, we view each security challenge as an opportunity to refine and enhance protection for our clients.
Choosing Vadimages means choosing a partner who understands that website security is never “set and forget.” We bring not just technology, but real-world expertise, practical strategies, and a relentless commitment to your business continuity.
Trust Vadimages for Security-First Web Development
Security breaches are inevitable—but disaster is not. With proactive detection, rapid response, and continuous improvement, your website can withstand the challenges of today’s threat landscape and emerge stronger than ever. Whether you need a security audit, incident response planning, or end-to-end development with security built in, Vadimages is ready to help. Contact us today to ensure your business remains secure, resilient, and ready for the future.
