The Coverage Crisis: Why Claims Get Denied
Cyber insurers in the United States paid out more than $2.4 billion for ransomware and data-breach losses last year, yet nearly a quarter of submitted claims were rejected outright. The fine print is brutal: if an SMB cannot prove that it enforced basic controls—multi-factor authentication on admin accounts, immutable backups, documented patch cadence—carriers can classify the incident as “avoidable.” That single word flips a six-figure payout into zero dollars. The message is clear. A cyber policy is no longer a safety net you buy; it is an exam you must pass. And the exam is getting harder each renewal cycle as underwriters tighten questionnaires and send third-party scanners to probe public-facing websites for out-of-date libraries, weak TLS ciphers, and forgotten admin panels.
The Core Checklist Insurers Use in 2025
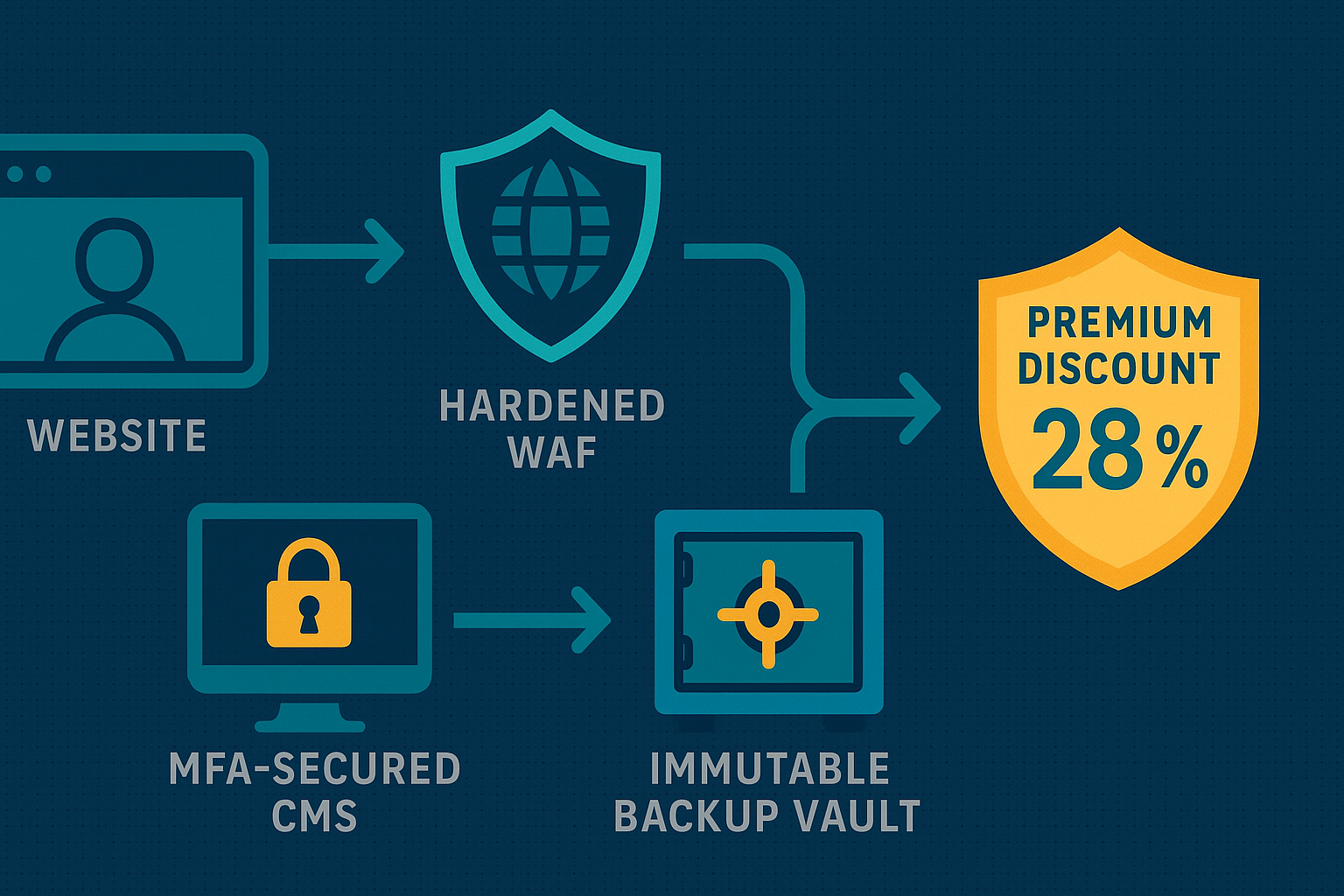
Underwriting teams have converged on a practical, if unforgiving, compliance template. First, Multi-Factor Authentication is mandatory on every privileged login—the CMS backend, Git repository, hosting control panel, even the marketing automation console. Second, Endpoint Detection & Response has become the minimum line of defense, replacing legacy antivirus with 24×7 behavioral monitoring that can quarantine rogue scripts before they exfiltrate customer data. Third, air-gapped or cloud-based immutable backups must demonstrate a “15-minute recovery point objective” and prove they are unreachable from the production network. Fourth, continuous vulnerability management is expected: monthly patch windows and WAF rules that auto-block emerging OWASP threats. Finally, every employee must complete security-awareness training, with phishing-simulation scores archived as evidence. Insurers call this combination the “cyber insurance checklist,” and they will refuse coverage, or jack up premiums, for any missing element.
Closing Your Gaps in 90 Days: The Vadimages Method
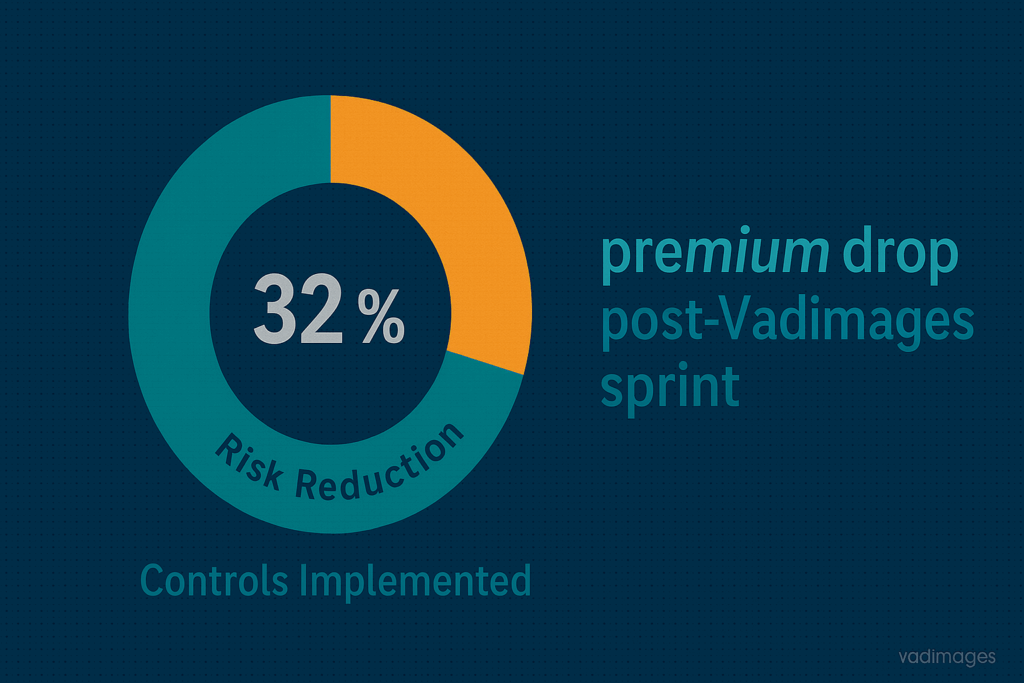
Most small and mid-sized businesses do not fail the checklist for lack of will; they fail for lack of bandwidth. That is exactly where Vadimages steps in. Our Web Security Sprint compresses a year of piecemeal hardening into twelve focused weeks: week 1 begins with attack-surface mapping and a live penetration test; week 4 locks down admin paths behind conditional MFA; week 7 migrates from outdated SHA-1 certificates to TLS 1.3; week 10 re-platforms nightly site backups onto immutable S3 Object Lock; week 12 culminates with a simulated claim scenario and a signed attestation you hand directly to your broker. Clients typically see premium reductions between 18 and 32 percent on renewal and, more importantly, achieve the confidence that a future breach will not morph into a claim dispute. If your policy renewal questionnaire is sitting unanswered in your inbox, book a call today and let Vadimages turn red flags into green lights.
Future-Proofing Compliance for U.S. SMBs

Regulations are shifting from recommendation to requirement. The SEC’s new incident-disclosure rule fines public companies that cannot file a Form 8-K within four days of material breach discovery. Thirteen states now impose ransomware-payment reporting within 24 hours, and federal regulators are signaling support for a national safe-harbor law that rewards businesses able to demonstrate “reasonable security.” Each of these initiatives leans on the same technical safeguards insurers already demand. By aligning your website architecture with the cyber-insurance baseline now, you avoid scrambling later when regulators or enterprise customers issue their own due-diligence questionnaires. Security is no longer a cost center; it is the price of entry to bigger contracts, lower premiums, and uninterrupted growth in an economy where trust is becoming the ultimate currency. Vadimages stands ready to engineer that trust into every pixel and packet of your digital presence.
